1D0-571 CIW v5 Security Essentials Questions and Answers
You have been assigned to configure a DMZ that uses multiple firewall components. Specifically, you must configure a router that will authoritatively monitor and, if necessary, block traffic. This device will be the last one that inspects traffic before it passes to the internal network. Which term best describes this device?
Consider the following image of a packet capture:
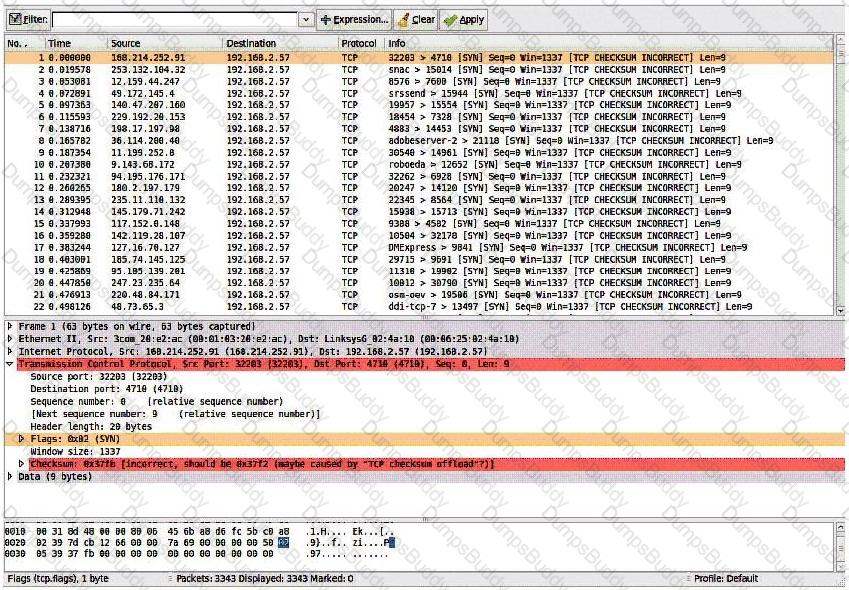
This packet capture has recorded two types of attacks. Which choice lists both attack types?
You have discovered that the ls, su and ps commands no longer function as expected. They do not return information in a manner similar to any other Linux system. Also, the implementation of Tripwire you have installed on this server is returning new hash values. Which of the following has most likely occurred?
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?


