In the Check Point Firewall Kernel Module, each Kernel is associated with a key, which specifies the type of traffic applicable to the chain module. For Stateful Mode configuration, chain modules marked with ___________ will not apply.
Your users are defined in a Windows 2008 R2 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in R80?
You have configured Automatic Static NAT on aninternal host-node object. You clear the box Translate destination on client site from Global Properties > NAT. Assuming all other NAT settings in Global Properties are selected, what else must be configured so that a host on the Internet can initiate an inbound connection to this host?
How do you recover communications between your Security Management Server and Security Gateway if you lock yourself out through a rule or policy mis-configuration?
Which command would provide the most comprehensive diagnostic information to Check Point Technical Support?
Complete this statement from the options provided. Using Captive Portal, unidentified users may be either; blocked, allowed to enter required credentials, or required to download the _____________.
You are running a R80 Security Gateway on GAiA. In case of a hardware failure, you have a server with the exact same hardware and firewall version installed. What back up method could be used to quickly put the secondary firewall into production?
Captive Portal is a __________ that allows the gateway to request login information from the user.
You find that Users are not prompted for authentication when they access their Web servers, even though you havecreated an HTTP rule via User Authentication. Choose the BEST reason why.
You are the Security Administrator for MegaCorp. A Check Point firewall isinstalled and in use on a platform using GAiA. You have trouble configuring the speed and duplex settings of your Ethernet interfaces. Which of the following commands can be used in CLISH to configure the speed and duplex settings of an Ethernet interfaceand will survive a reboot? Give the BEST answer.
When restoring R80 using the command upgrade_import, which of the following items are NOT restored?
ALL of the following options are provided by the GAiAsysconfig utility, EXCEPT:
Which of the following commands can provide the most complete restoration of a R80 configuration?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimizemalware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants tomove around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
You want to implement Static Destination NAT in order to provide external, Internet users access to an internal Web Serverthat has a reserved (RFC 1918) IP address. You have an unused valid IP address on the network between your Security Gateway and ISP router. You control the router that sits between the firewall external interface and the Internet.
What is an alternative configuration if proxy ARP cannot be used on your Security Gateway?
Which Check Point address translation method is necessary if you want to connect from a host on the Internet via HTTP to a server with a reserved (RFC 1918) IP address on your DMZ?
You intend to upgrade a Check Point Gateway from R71 to R80. Prior to upgrading, you want to back up the Gateway should there be any problems with the upgrade. Which of the following allows for the Gateway configuration to be completely backed up into a manageable size in the least amount of time?
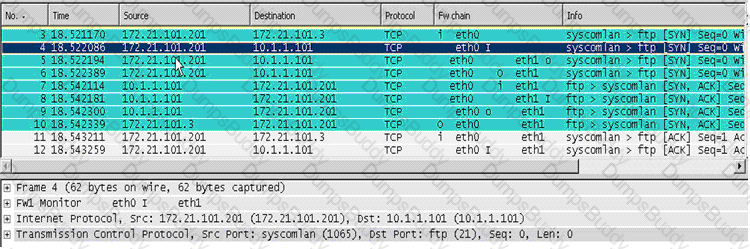
Looking at the SYN packets in the Wireshark output, select the statement that is true about NAT.
Several Security Policies can be used for different installation targets. The Firewall protecting Human Resources’ servers should have its own Policy Package. These rules must be installed on this machine and not onthe Internet Firewall. How can this be accomplished?
Before upgrading SecurePlatform to GAiA, you should create a backup. To save time, many administrators use the command backup. This creates a backupof the Check Point configuration as well as the system configuration.
An administrator has installed the latest HFA on the system for fixing traffic problem after creating a backup file. There is a mistake in the very complex static routing configuration.The Check Point configuration has not been changed. Can the administrator use a restore to fix the errors in static routing?
Security Gateway R80 supports UserAuthentication for which of the following services? Select the response below that contains the MOST correct list of supported services.
The technical-support department has a requirement to access an intranet server. When configuring a User Authentication rule to achieve this, whichof the following should you remember?
Which of the following options is available with the GAiA cpconfig utility on a Management Server?
You are the Security Administrator for ABC-Corp. A Check Point Firewall is installed and in use on GAiA. You are concerned that the system might not be retaining your entries for the interfaces and routing configuration. You would like to verify your entries in the corresponding file(s) on GAiA. Where can you view them? Give the BEST answer.
The third-shift Administrator was updating Security Management Server access settings in Global Properties. He managed to lock all administrators out of their accounts. How should you unlock these accounts?
What mechanism does a gateway configured with Identity Awareness and LDAP initially use to communicate with aWindows 2003 or 2008 server?
You have selected the event Port Scanfrom Internal Network in SmartEvent, to detect an event when 30 port scans have occurred within 60 seconds. You also want to detect two port scans from a host within 10 seconds of each other. How would you accomplish this?
How many pre-defined exclusions are included by default in SmartEvent R80 as part of the product installation?
Fill in the blank. To remove site-to-site IKE and IPSEC keys you would enter command ____ ___ and select the option to delete all IKE and IPSec SA’s.
What command syntax would you use to turn on PDP logging in a distributed environment?
If you need strong protection for the encryption of user data, what option would be the BEST choice?
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an externalpartner. Which of the following activities should you do first?
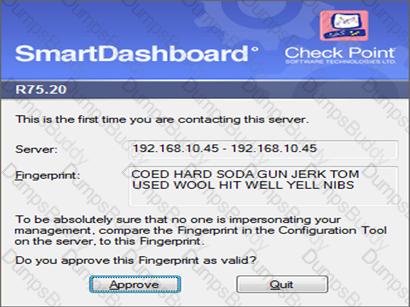
How could you compare the Fingerprint shown to the Fingerprint on the server? Run cpconfig and select:
Exhibit:
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a newadministrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
Type the full fw command and syntax that allows you to disable only sync on a cluster firewall member.
Fill in the blanks. To view the number of concurrent connections going through your firewall, you would use the command and syntax __ ___ __ __________ __ .
To bind a NIC to a single processor when using CoreXL on GAiA, you would use the command
How could you compare the Fingerprint shown to the Fingerprint on the server?
Exhibit:
MultiCorp is located in Atlanta. It has a branch office in Europe, Asia, and Africa. Each location has its own AD controller for local user login. How many ADqueries have to be configured?
When configuring numbered VPN Tunnel Interfaces (VTIs) in a clustered environment, what issues need to be considered?
1) Each member must have a unique source IP address.
2) Every interface on each member requires a unique IP address.
3) All VTI's going to the same remote peer musthave the same name.
4) Cluster IP addresses are required.
When migrating the SmartEvent data base from one server to another, the last step is to save the files on the new server. Which of thefollowing commands should you run to save the SmartEvent data base files on the new server?
Which of the following items should be configured for the Security Management Server to authenticate via LDAP?
To qualify as an Identity Awareness enabled rule, which column MAY include an Access Role?
What is the purpose of the pre-defined exclusions included with SmartEvent R80?
Fill in the blanks. To view thenumber of concurrent connections going through core 0 on the firewall, you would use the command and syntax __ __ _ ___ __ ___________ __ .
Type the command and syntax that you would use to view thevirtual cluster interfaces of a ClusterXL environment.
Your company has the requirement that SmartEvent reports should show a detailed and accurate view of network activity but also performance should beguaranteed. Which actions should be taken to achieve that?
1) Use same hard drive for database directory, log files, and temporary directory.
2) Use Consolidation Rules.
3) Limit logging to blocked traffic only.
4) Use Multiple Database Tables.
Which is a suitable command to check whether Drop Templates are activated or not?
Which one ofthe following processes below would not start if there was a licensing issue.
True or False: SecureXL improves non-ecnrypted firewall traffic throughput and encrypted VPN traffic
throughput.
Choose the correct syntax to add a new host named “emailserver1” with IP address 10.50.23.90 using GAiA Management CLI?
Joey and Vanessa arefirewall administrators in their company. Joey wants to run Management API server on his Security Management server. He is logging in to a Smart Console and goes to the Manage & Settings > Blade. In Management API section, he proceeds to Advanced Settings.He likes to set up the Management API server to automatic run at startup. He is surprised, because this functionality is already selected by default.
What is the reason, that functionality is already enabled?
Both ClusterXL and VRRP are fully supported by Gaia R80.10 and available to all Check Point appliances. Which of the following command is NOT related to redundancy and functions?
What is correct statement about Security Gateway and Security Management Server failover in Check Point R80.X in terms of Check Point Redundancy driven solutions?
Fred is troubleshooting a NAT issue and wants to check to see if the inboundconnection from his internal network is being translated across the interface in the firewall correctly. He decides to use the fw monitor to capture the traffic from the source 192.168.3.5 or the destination of 10.1.1.25 on his Security Gateway, Green thathas an IP of 192.168.4.5. What command captures this traffic in a file that he can download and review with WireShark?
As an administrator, you may berequired to add the company logo to reports. To do this, you would save the logo as a PNG file with the name ‘cover-company-logo.png’ and then copy that image file to which directory on the SmartEvent server?
In order to get info about assignment (FW, SND) of all CPUs in your SGW, what is themost accurate CLI command?
SmartEvent has several components that function together to track security threats. What is the function of the Correlation Unit as a component of this architecture?