Fill in the blank.
In Load Sharing Unicast mode, the internal cluster IP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2. Internal host 10.4.8.108 Pings 10.4.8.3, and receives replies. The following is the ARP table from the internal Windows host 10.4.8.108.
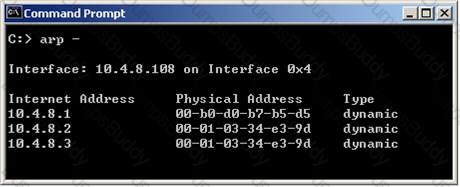
Review the exhibit and type the IP address of the member serving as the pivot machine in the space below.
Which of the following log files contains verbose information regarding the negotiation process and other encryption failures?
You have three Gateways in a mesh community. Each gateway’s VPN Domain is their internal network as defined on the Topology tab setting All IP Addresses behind Gateway based on Topology information.
You want to test the route-based VPN, so you created VTIs among the Gateways and created static route entries for the VTIs. However, when you test the VPN, you find out the VPN still go through the regular domain IPsec tunnels instead of the routed VTI tunnels.
What is the problem and how do you make the VPN use the VTI tunnels?
Which of the following is TRUE concerning numbered VPN Tunnel Interfaces (VTIs)?
When using Captive Portal to send unidentified users to a Web portal for authentication, which of the following is NOT a recommended use for this method?
Which is NOT a method through which Identity Awareness receives its identities?
In a Management High Availability (HA) configuration, you can configure synchronization to occur automatically, when:
1. The Security Policy is installed.
2. The Security Policy is saved.
3. The Security Administrator logs in to the secondary SmartCenter Server, and changes its status to active.
4. A scheduled event occurs.
5. The user database is installed.
Select the BEST response for the synchronization sequence. Choose one.
Which of the following describes the default behavior of an R77 Security Gateway?
Which graded parameters help determine the protections to activate for security and which can be safely deactivated? Select the most correct answer.
Frank is concerned with performance and wants to configure the affinities settings. His gateway does not have the Performance pack running. What would Frank need to perform in order configure those settings?
Katie has enabled User Directory and applied the license to Security Management Server, Green. Her supervisor has asked her to configure the Password Strength options of the least one digit, one symbol, 8 characters long and include an uppercase character. How should she accomplish this?
You have pushed a policy to your firewall and you are not able to access the firewall. What command will allow you to remove the current policy from the machine?
Lilly has generated an IKE debug on her Security Gateway. She has asked Jack to transfer the file to Support. Where is the file located?
In GAiA, if one is unsure about a possible command, what command lists all possible commands.
MicroCorp experienced a security appliance failure. (LEDs of all NICs are off.) The age of the unit required that the RMA-unit be a different model. Will a revert to an existing snapshot bring the new unit up and running?
You are the MegaCorp Security Administrator. This company uses a firewall cluster, consisting of two cluster members. The cluster generally works well but one day you find that the cluster is behaving strangely. You assume that there is a connectivity problem with the cluster synchronization link (cross-over cable). Which of the following commands is the BEST for testing the connectivity of the crossover cable?
What is the proper CLISH syntax to configure a default route via 192.168.255.1 in GAiA?
Where do you define NAT properties so that NAT is performed either client side or server side? In SmartDashboard under:
What firewall kernel table stores information about port allocations for Hide NAT connections?
Fill in the blank.
To bind a NIC to a single processor when using CoreXL on GAiA, you would use the command
Fill in the blank with a numeric value. The default port number for Secure Sockets Layer (SSL) connections with the LDAP Server is
Which three of the following are ClusterXL member requirements?
1) same operating systems
2) same Check Point version
3) same appliance model
4) same policy
MegaCorp plans to upgrade all of its firewalls. Currently the corporation is a mixture of SecurePlatform and IPSO machines running R71, to the latest code level of GAiA. Many of the firewalls are using VTIs to allow advanced routing configuration to propagate through all the networks. What will the Acme company need to do to make sure VTIs will work once moved to GAiA?
MegaCorp is running Smartcenter R70, some Gateways at R65 and some other Gateways with R60. Management wants to upgrade to the most comprehensive IPv6 support. What should the administrator do first?
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
MultiCorp is running Smartcenter R71 on an IPSO platform and wants to upgrade to a new Appliance with R77. Which migration tool is recommended?
Which of the following CLISH commands would you use to set the admin user's shell to bash?
How could you compare the Fingerprint shown to the Fingerprint on the server? Run cpconfig and select:
Exhibit:
Control connections between the Security Management Server and the Gateway are not encrypted by the VPN Community. How are these connections secured?
Which of the following is a valid Active Directory designation for user John Doe in the Sales department of AcmeCorp.com?
Included in the customer’s network are some firewall systems with the Performance Pack in use. The customer wishes to use these firewall systems in a cluster (Load Sharing mode). He is not sure if he can use the Sticky Decision Function in this cluster. Explain the situation to him.
Where multiple SmartDirectory servers exist in an organization, a query from one of the clients for user information is made to the servers based on a priority. By what category can this priority be defined?
When migrating the SmartEvent data base from one server to another, the last step is to save the files on the new server. Which of the following commands should you run to save the SmartEvent data base files on the new server?
What is the supported ClusterXL configuration when configuring a cluster synchronization network on a VLAN interface?
To clean the system of all SmartEvent events, you should delete the files in which folder(s)?
Where is it necessary to configure historical records in SmartView Monitor to generate Express reports in SmartReporter?
In which ClusterXL Load Sharing mode, does the pivot machine get chosen automatically by ClusterXL?
Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). Which of the following is NOT a recommended use for this method?
MultiCorp has bought company OmniCorp and now has two active AD domains. How would you deploy Identity Awareness in this environment?
In the following cluster configuration; if you reboot sglondon_1 which device will be active when sglondon_1 is back up and running? Why?
Which of the following access options would you NOT use when configuring Captive Portal?
If using AD Query for seamless identity data reception from Microsoft Active Directory (AD), which of the following methods is NOT Check Point recommended?
Jerry is concerned that a denial-of-service (DoS) attack may affect his VPN Communities. He decides to implement IKE DoS protection. Jerry needs to minimize the performance impact of implementing this new protection.
Which of the following configurations is MOST appropriate for Jerry?
How can you prevent delay-sensitive applications, such as video and voice traffic, from being dropped due to long queue using Check Point QoS solution?
If Victor wanted to edit new Signature Protections, what tab would he need to access in SmartDashboard?
You plan to migrate a VPN-1 NG with Application Intelligence (Al) R55 SmartCenter Server to VPN-1 NGX. You also plan to upgrade four VPN-1 Pro Gateways at remote offices, and one local VPN-1 Pro Gateway at your company's headquarters. The SmartCenter Server configuration must be migrated. What is the correct procedure to migrate the configuration?
You have installed a R77 Security Gateway on GAiA. To manage the Gateway from the enterprise Security Management Server, you create a new Gateway object and Security Policy.
When you install the new Policy from the Policy menu, the Gateway object does not appear in the Install Policy window as a target. What is the problem?
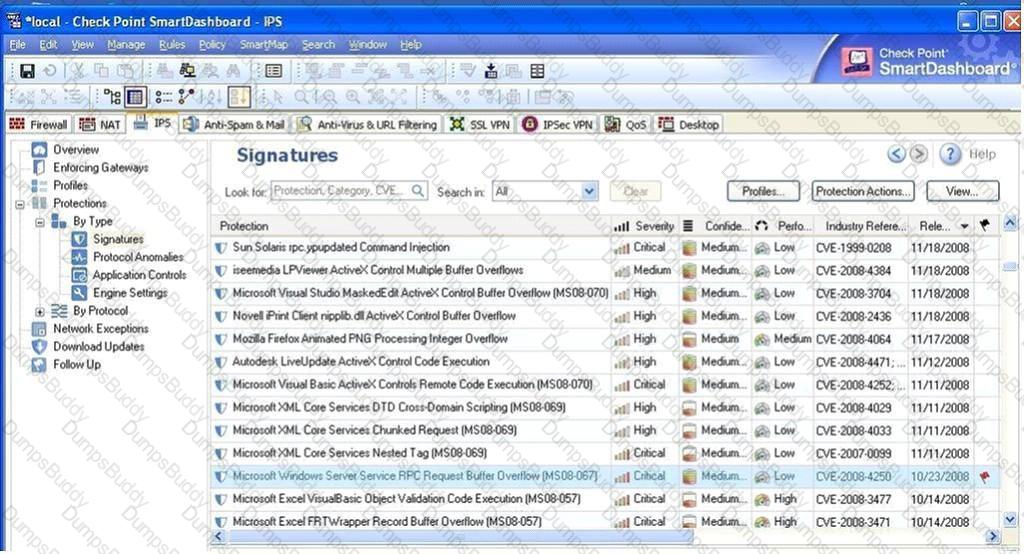
Using the output below, what does the red flag indicate for the MS08-067 Protection?
You need to completely reboot the Operating System after making which of the following changes on the Security Gateway? (i.e. the command cprestart is not sufficient.)
1. Adding a hot-swappable NIC to the Operating System for the first time.
2. Uninstalling the R75 Power/UTM package.
3. Installing the R75 Power/UTM package.
4. Re-establishing SIC to the Security Management Server.
5. Doubling the maximum number of connections accepted by the Security Gateway.
What is the most typical type of configuration for VPNs with several externally managed Gateways?
When selecting a backup target using SmartProvisioning, which target is NOT available?
You are a Security Administrator preparing to deploy a new HFA (Hot fix Accumulator) to ten Security Gateways at five geographically separated locations.
What is the BEST method to implement this HFA?
For an initial installation of Connecter, which of the following statements is TRUE?
What happens in relation to the CRL cache after a cpstop;spstart has been initiated?
You want to upgrade an NG with Application Intelligence R55 Security Gateway running on SecurePlatform to VPN-1 NGX R65 via SmartUpdate.
Which package(s) is(are) needed in the Repository prior to upgrade?
Cody is notified by blacklist.org that his site has been reported as a spam relay, due to his SMTP Server being unprotected. Cody decides to implement an SMTP Security Server, to prevent the server from being a spam relay.
Which of the following is the most efficient configuration method?
SmartProvisioning uses different types of profiles to manage and provision the gateways.
These types are:
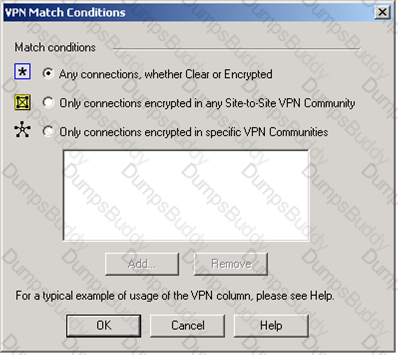
You want VPN traffic to match packets from internal interfaces. You also want the traffic to exit the Security Gateway bound for all site-to-site VPN Communities, including Remote Access Communities. How should you configure the VPN match rule?
Your organization maintains several IKE VPN’s. Executives in your organization want to know which mechanism Security Gateway R77 uses to guarantee the authenticity and integrity of messages. Which technology should you explain to the executives?
You are trying to configure Directional VPN Rule Match in the Rule Base. But the Match column does not have the option to see the Directional Match. You see the following window. What must you enable to see the Directional Match?
Exhibit:
Remote clients are using IPSec VPN to authenticate via LDAP server to connect to the organization. Which gateway process is responsible for the authentication?
The connection to the ClusterXL member ‘A’ breaks. The ClusterXL member ‘A’ status is now ‘down’. Afterwards the switch admin set a port to ClusterXL member ‘B’ to ‘down’. What will happen?
Fill in the blank.
Type the command and syntax that you would use to view the virtual cluster interfaces of a ClusterXL environment.
_____ is the called process that starts when opening SmartView Tracker application.