Which of the following is considered to be the more secure and preferred VPN authentication method?
John is the administrator of a R80 Security Management server managing r R77.30 Check Point Security Gateway. John is currently updating the network objects and amending the rules using SmartConsole. To make John’s changes available to other administrators, and to save the database before installing a policy, what must John do?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
After the initial installation the First Time Configuration Wizard should be run. Select the BEST answer.
Fill in the blank: Once a license is activated, a ________ should be installed.
You want to reset SIC between smberlin and sgosaka.
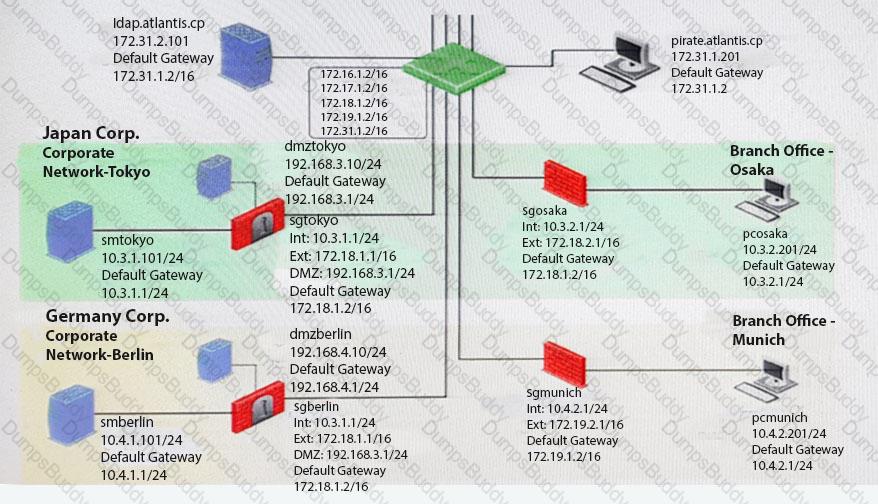
In SmartDashboard, you choose sgosaka, Communication, Reset. On sgosaka, you start cpconfig, choose Secure Internal Communication and enter the new SIC Activation Key. The screen reads The SIC was successfully initialized and jumps back to the menu. When trying to establish a connection, instead of a working connection, you receive this error message:
What is the reason for this behavior?
Fill in the blanks: A Check Point software license consists of a _______ and _______ .
Fill in the blanks: A High Availability deployment is referred to as a ______ cluster and a Load Sharing deployment is referred to as a ________ cluster.
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office. What is the correct order for pushing SIC certificates to the Gateway before shipping it?
1. Run cpconfig on the Gateway, select Secure Internal Communication, enter the activation key, and reconfirm.
2. Initialize Internal Certificate Authority (ICA) on the Security Management Server.
3. Configure the Gateway object with the host name and IP addresses for the remote site.
4. Click the Communication button in the Gateway object's General screen, enter the activation key, and click Initialize and OK.
5. Install the Security Policy.
In the R80 SmartConsole, on which tab are Permissions and Administrators defined?
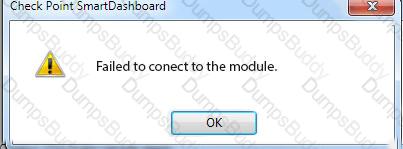
On the following picture an administrator configures Identity Awareness:
After clicking “Next” the above configuration is supported by:
What is the potential downside or drawback to choosing the Standalone deployment option instead of the Distributed deployment option?
Fill in the blank: The IPS policy for pre-R80 gateways is installed during the _______ .
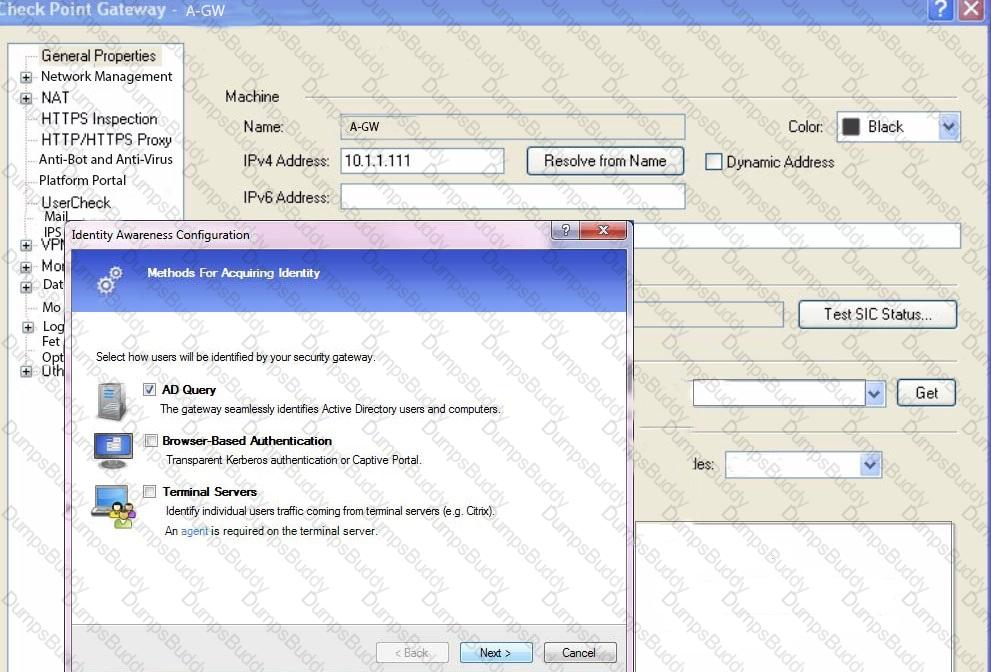
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the “Select additional profile that will be able edit this layer” you do not see anything. What is the most likely cause of this problem? Select the BEST answer.
Which SmartConsole component can Administrators use to track changes to the Rule Base?
The fw monitor utility is used to troubleshoot which of the following problems?
Fill in the blanks: A security Policy is created in _________ , stored in the _________ , and Distributed to the various __________ .
AdminA and AdminB are both logged in on SmartConsole. What does it mean if AdminB sees a locked icon on a rule? Choose the BEST answer.
Fill in the blank: The R80 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows them as prioritized security events.
Fill in the blank: The R80 utility fw monitor is used to troubleshoot _____________
In which deployment is the security management server and Security Gateway installed on the same appliance?
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
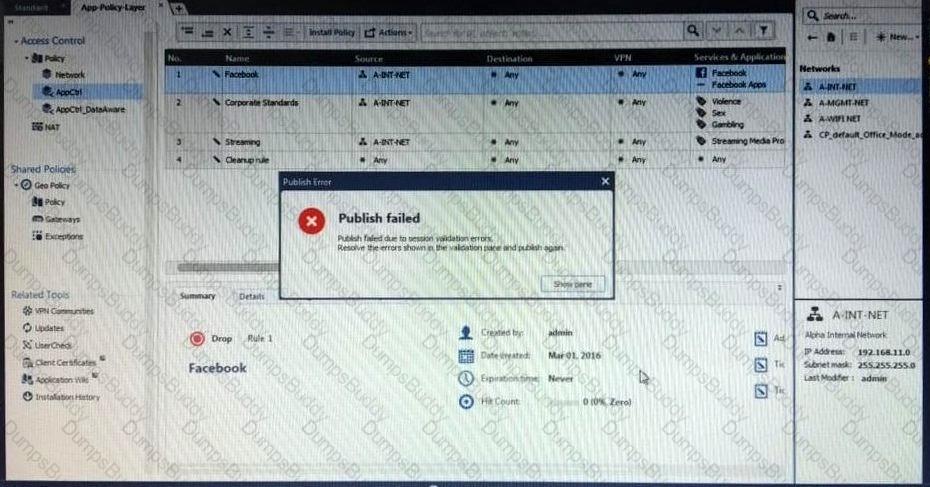
Administrator Kofi has just made some changes on his Management Server and then clicks on the Publish button in SmartConsole but then gets the error message shown in the screenshot below.
Where can the administrator check for more information on these errors?
Which utility allows you to configure the DHCP service on GAIA from the command line?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
Which Threat Prevention Software Blade provides comprehensive against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
Fill in the blank: With the User Directory Software Blade, you can create R80 user definitions on a(an) ___________ Server.
With which command can you view the running configuration of Gaia-based system.
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
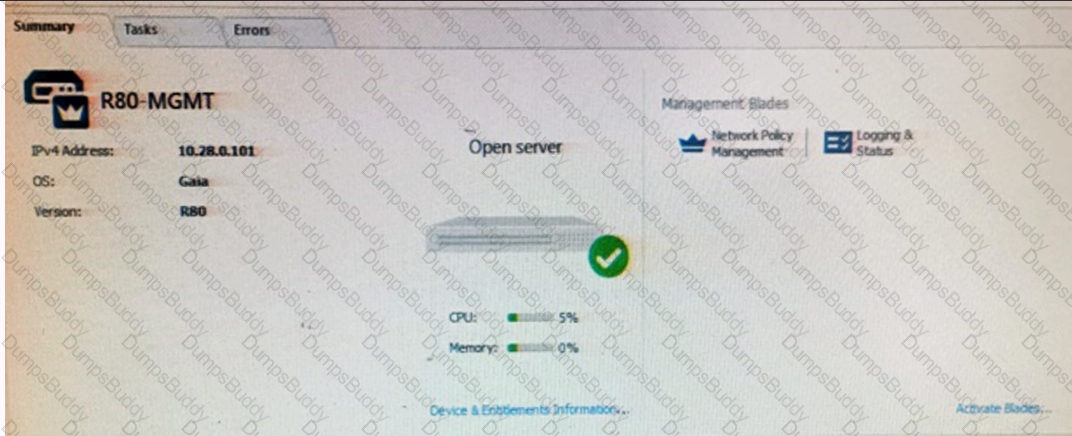
Tina is a new administrator who is currently reviewing the new Check Point R80 Management console interface. In the Gateways view, she is reviewing the Summary screen as in the screenshot below. What as an 'Open Server'?
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
View the rule below. What does the lock-symbol in the left column mean? Select the BEST answer.

Which of the following Windows Security Events will NOT map a username to an IP address in Identity Awareness?
Fill in the blank: Each cluster, at a minimum, should have at least ___________ interfaces.
Which backup utility captures the most information and tends to create the largest archives?
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
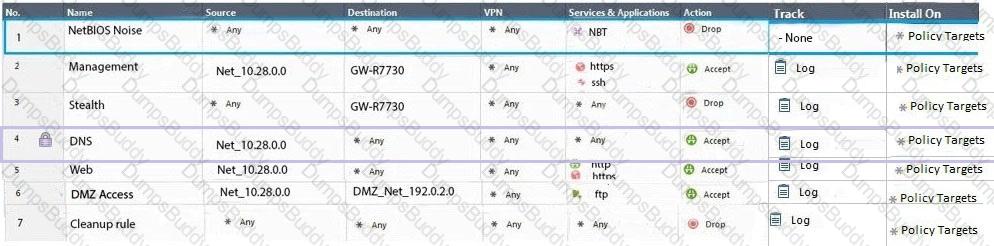
What is the possible explanation for this?
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
MegaCorp's security infrastructure separates Security Gateways geographically. You must request a central license for one remote Security Gateway.
How do you apply the license?
Which of the following is NOT a valid option when configuring access for Captive Portal?
According to Check Point Best Practice, when adding a non-managed Check Point Gateway to a Check Point security solution what object SHOULD be added? A(n):
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
You have configured SNX on the Security Gateway. The client connects to the Security Gateway and the user enters the authentication credentials. What must happen after authentication that allows the client to connect to the Security Gateway's VPN domain?
You are using SmartView Tracker to troubleshoot NAT entries. Which column do you check to view the NAT'd source port if you are using Source NAT?
How do you configure the Security Policy to provide uses access to the Captive Portal through an external (Internet) interface?
The WebUI offers three methods for downloading Hotfixes via CPUSE. One of them is Automatic method. How many times per day will CPUSE agent check for hotfixes and automatically download them?
You find a suspicious connection from a problematic host. You decide that you want to block everything from that whole network, not just the problematic host. You want to block this for an hour while you investigate further, but you do not want to add any rules to the Rule Base. How do you achieve this?
You have two rules, ten users, and two user groups in a Security Policy. You create database version 1 for this configuration. You then delete two existing users and add a new user group. You modify one rule and add two new rules to the Rule Base. You save the Security Policy and create database version 2. After a while, you decide to roll back to version 1 to use the Rule Base, but you want to keep your user database. How can you do this?
Using mgmt_cli, what is the correct syntax to import a host object called Server_1 from the CLI?
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?