You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities should you do first?
An internal router is sending UDP keep-alive packets that are being encapsulated with GRE and sent through your R77 Security Gateway to a partner site. A rule for GRE traffic is configured for ACCEPT/LOG. Although the keep-alive packets are being sent every minute, a search through the SmartView Tracker logs for GRE traffic only shows one entry for the whole day (early in the morning after a Policy install).
Your partner site indicates they are successfully receiving the GRE encapsulated keep-alive packets on the 1-minute interval.
If GRE encapsulation is turned off on the router, SmartView Tracker shows a log entry for the UDP keep-alive packet every minute.
Which of the following is the BEST explanation for this behavior?
You are the Security Administrator for MegaCorp. In order to see how efficient your firewall Rule Base is, you would like to see how often the particular rules match. Where can you see it? Give the BEST answer.
True or False. SmartView Monitor can be used to create alerts on a specified Gateway.
Review the rules.
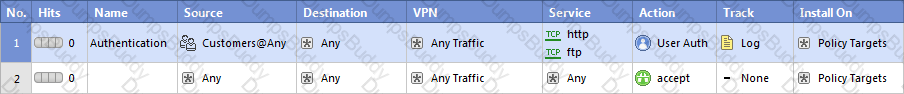
Assume domain UDP is enabled in the impled rules.
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
Which R77 GUI would you use to see the number of packets accepted since the last policy install?
In the Rule Base displayed for fwsingapore, user authentication in Rule 4 is configured as fully automatic. Eric is a member of the LDAP group, MSD_Group.
What happens when Eric tries to connect to a server on the Internet?
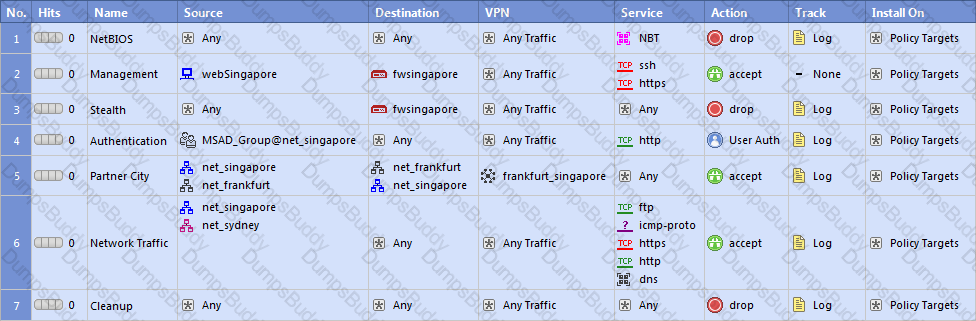
When configuring LDAP authentication, which of the following items should be configured for the Security Management Server?
Jack has locked himself out of the Kirk Security Gateway with an incorrect policy and can no longer connect from the McCoy Management Server.
Jack still has access to an out of band console connection on the Kirk Security Gateway. He is logged into the Gaia CLI, what does he need to enter in order to be able to fix his mistake and push policy?
Which authentication type requires specifying a contact agent in the Rule Base?
Lily has completed the initial setup of her Management Server with an IP address of 192.168.12.12. She must now run the First Time Configuration Wizard via the Gaia Portal to finish the setup. Lily knows she must use a browser to access the device, but it unsure of the correct URL to enter; which one below will she need to use?
What is one potential downside or drawback to choosing the Standalone deployment option instead of the Distributed deployment option?
In SmartDashboard, you configure 45 MB as the required free hard-disk space to accommodate logs. What can you do to keep old log files, when free space falls below 45 MB?
Central license management allows a Security Administrator to perform which of the following functions?
1. Check for expired licenses.
2. Sort licenses and view license properties.
3. Attach both R77 Central and Local licesnes to a remote module.
4. Delete both R77 Local Licenses and Central licenses from a remote module.
5. Add or remove a license to or from the license repository.
6. Attach and/or delete only R77 Central licenses to a remote module (not Local licenses).
An Administrator without access to SmartDashboard installed a new IPSO-based R77 Security Gateway over the weekend. He e-mailed you the SIC activation key and the IP address of the Security Gateway. You want to confirm communication between the Security Gateway and the Management Server by installing the Policy. What might prevent you from installing the Policy?
You have detected a possible intruder listed in SmartView Tracker’s active pane. What is the fastest method to block this intruder from accessing your network indefinitely?
Which SmartView Tracker mode allows you to read the SMTP e-mail body sent from the Chief Executive Officer (CEO) of a company?
Which R77 feature or command allows Security Administrators to revert to earlier Security Policy versions without changing object configurations?
You have a diskless appliance platform. How do you keep swap file wear to a minimum?
You have configured Automatic Static NAT on an internal host-node object. You clear the box Translate destination on client site from Global Properties > NAT. Assuming all other NAT settings in Global Properties are selected, what else must be configured so that a host on the Internet can initiate an inbound connection to this host?
When restoring R77 using the command upgrade_import, which of the following items are NOT restored?
Your organization’s disaster recovery plan needs an update to the backup and restore section to reap the new distributed R77 installation benefits. Your plan must meet the following required and desired objectives:
Required ObjectivE. The Security Policy repository must be backed up no less frequently than every 24 hours.
Desired ObjectivE. The R77 components that enforce the Security Policies should be backed up at least once a week.
Desired ObjectivE. Back up R77 logs at least once a week.
Your disaster recovery plan is as follows:
- Use the cron utility to run the command upgrade_export each night on the Security Management Servers.
- Configure the organization's routine back up software to back up the files created by the command upgrade_export.
- Configure the GAiA back up utility to back up the Security Gateways every Saturday night.
- Use the cron utility to run the command upgrade_export each Saturday night on the log servers.
- Configure an automatic, nightly logswitch.
- Configure the organization's routine back up software to back up the switched logs every night.
Upon evaluation, your plan:
Because of pre-existing design constraints, you set up manual NAT rules for your HTTP server. However, your FTP server and SMTP server are both using automatic NAT rules. All traffic from your FTP and SMTP servers are passing through the Security Gateway without a problem, but traffic from the Web server is dropped on rule 0 because of anti-spoofing settings.
What is causing this?
Where can an administrator specify the notification action to be taken by the firewall in the event that available disk space drops below 15%?
How granular may an administrator filter an Access Role with identity awareness? Per:
In a distributed management environment, the administrator has removed all default check boxes from the Policy > Global Properties > Firewall tab. In order for the Security Gateway to send logs to the Security Management Server, an explicit rule must be created to allow the Security Gateway to communicate to the Security Management Server on port ______.
You have configured SNX on the Security Gateway. The client connects to the Security Gateway and the user enters the authentication credentials. What must happen after authentication that allows the client to connect to the Security Gateway’s VPN domain?
How can you check whether IP forwarding is enabled on an IP Security Appliance?
The Tokyo Security Management Server Administrator cannot connect from his workstation in Osaka.
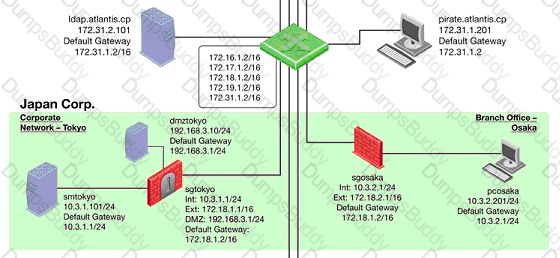
Which of the following lists the BEST sequence of steps to troubleshoot this issue?
An Administrator without access to SmartDashboard installed a new IPSO-based R77 Security Gateway over the weekend. He e-mailed you the SIC activation key. You want to confirm communication between the Security Gateway and the Management Server by installing the Policy. What might prevent you from installing the Policy?
The London Security Gateway Administrator has just installed the Security Gateway and Management Server. He has not changed any default settings. As he tries to configure the Gateway, he is unable to connect.
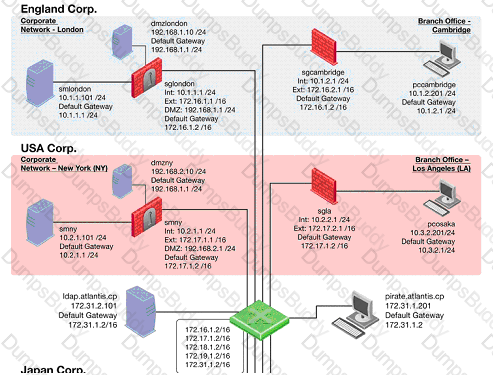
Which troubleshooting suggestion will NOT help him?
What command syntax would you use to see accounts the gateway suspects are service accounts?
What gives administrators more flexibility when configuring Captive Portal instead of LDAP query for Identity Awareness authentication?
How can you recreate the Security Administrator account, which was created during initial Management Server installation on GAiA?
How do you recover communications between your Security Management Server and Security Gateway if you lock yourself out through a rule or policy mis-configuration?
Which of the following firewall modes DOES NOT allow for Identity Awareness to be deployed?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned an IP address 10.0.0.19 via DHCP.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
Your company’s Security Policy forces users to authenticate to the Gateway explicitly, before they can use any services. The Gateway does not allow the Telnet service to itself from any location. How would you configure authentication on the Gateway? With a:
Which authentication type permits five different sign-on methods in the authentication properties window?
Which of the below is the MOST correct process to reset SIC from SmartDashboard?
When using AD Query to authenticate users for Identity Awareness, identity data is received seamlessly from the Microsoft Active Directory (AD). What is NOT a recommended usage of this method?