A firewall has 8 CPU cores and the correct license. CoreXL is enabled. How could you set kernel instance #3 to run on processing core #5?
What command displays the Connections Table for a specified CoreXL firewall instance?
When troubleshooting a performance problem on multicore firewall that is using CoreXL, what command checks the number of connections each core is processing?
Where in a fw monitor output would you see destination address translation occur in cases of inbound automatic static NAT?
Jane wants to create a VPN using OSPF. Which VPN configuration would you recommend she use?
You are configuring VTIs in a clustered environment. On Peer A the VTI name is VT_Cluster_GWA and on Peer B the VTI name is VT_Cluster_GWB. You find that the route-based tunnel is not coming up. What could be the cause?
What command would you use for a packet capture on an absolute position for TCP streaming (out) 1ffffe0
Which commands will properly set the debug level to maximum and then run a policy install in debug mode for the policy Standard on gateway A-GW from an R77 GAiA Management Server?
When you perform an install database, the status window is filled with large amounts of text. What could be the cause?
You run the command fwaccel conns and notice in the output that all the connections have “F” in the “flags” column, see below:
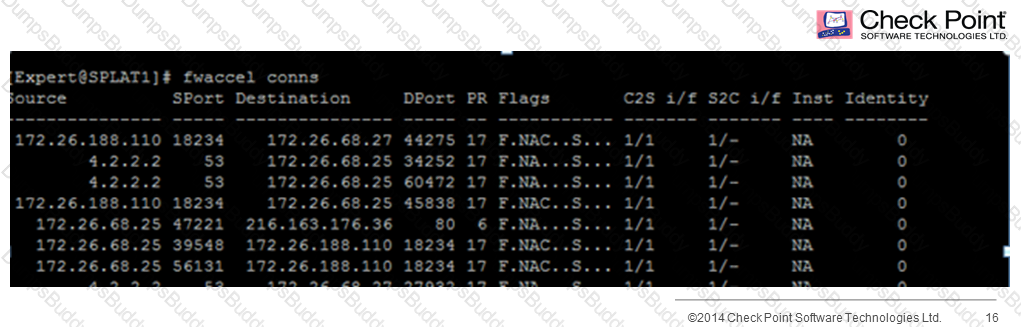
What does this mean?
Your ARP cache is overflowing negatively impacting users experience on your network. Which command can you issue to increase the ARP cache on the fly? You do not need this to survive reboot.
You are running some diagnostics on your GAIA gateway. You are reviewing the number of fragmented packets; you notice that there are a lot of large and duplicate packets. Which command did you issue to get this information?
Check Point Best Practices suggest that when you finish a kernel debug, you should run the command _____________________ .
Your company has recently decided to allow remote access for clients. You find that no one is able to connect, although you are confident that your rule set and remote access community has been defined correctly. What is the most likely cause, based on the options below? You have the following debug file:
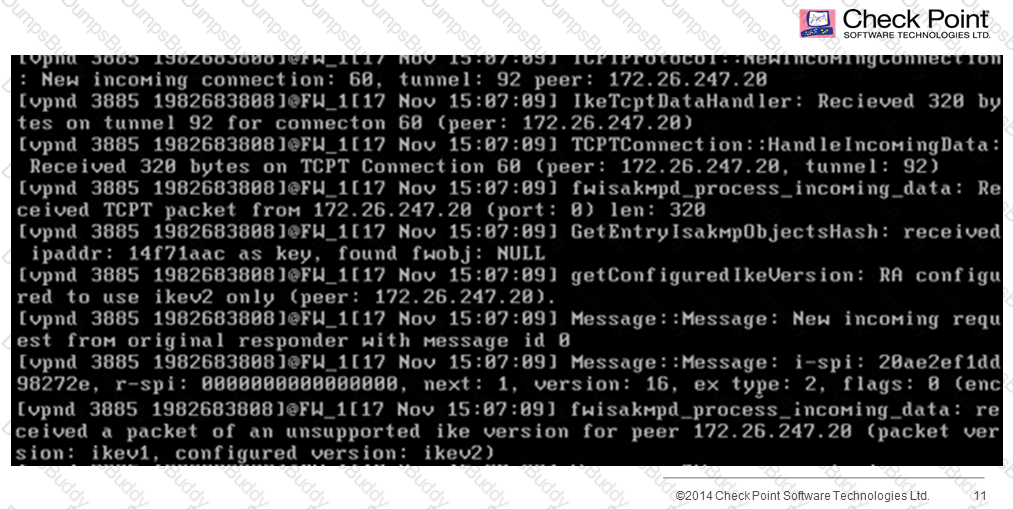
In a VPN configuration, the following mode can be used to increase throughput by bypassing firewall enforcement.
What is the log file that shows the keep alive packets during the debug process?
What would be considered Best Practice to determine which IPS protections you can safely disable for your environment?
Your Customer would like to enable IPS in his Corporate Cluster, but he is concerned about high CPU usage because if the IPS inspection. What feature would you configure to disable inspection if a high CPU usage develops?
After creating and pushing out a new policy, Joe finds that an old connection is still being allowed that should have been closed after his changes. He wants to delete the connection on the gateway, and looks it up with fw tab –t connections –u. Joe finds the connection he is looking for. What command should Joe use to remove this connection?
<0,a128c22,89,a158508,89,11;10001,2281,25,15b,a1,4ecdfeee,ac,691400ac,7b6,3e,ffffffff,3c,3c,0,0,0,0,0,0,0,0,0,0,0,0,0,0>
In order to prevent outgoing NTP traffic from being hidden behind a Cluster IP you should?
What is the best way to see how much traffic went through the firewall that was TCP, UDP and ICMP?
When a cluster member is completely powered down, how will the other member identify if there is network connectivity?
Misha is working on a stand-by firewall and deletes the connections table in error. He finds that now the table is out of sync with the Active member. to get them completely synced again, Mish should run the command pair ____________ and __________ .
Look at the follow Rule Base display. Rule 5 contains a TIME object. What is the effect on the following rules?
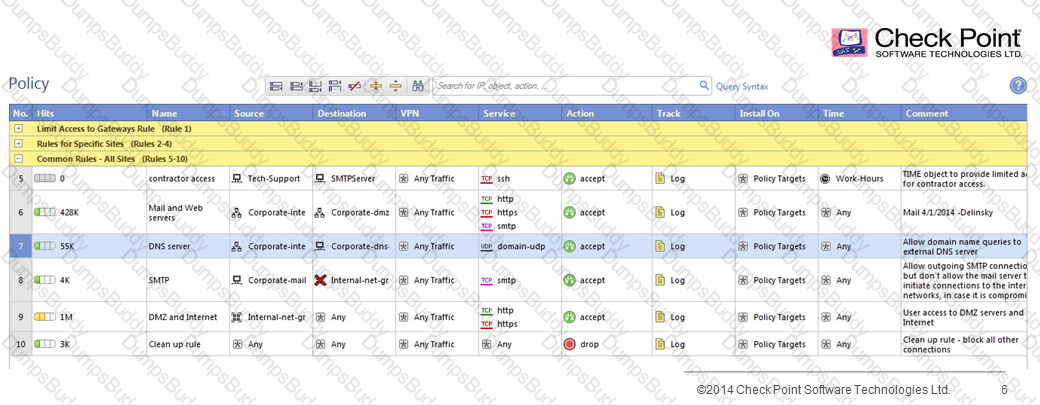
When optimizing a customer firewall Rule Base, what is the BEST way to start the analysis?
When are rules that include Identity Awareness Access (IDA) roles accelerated through SecureXL?
What is the command to check how many connections the firewall has detected for the SecureXL device?